The tech community is in a frenzy over malicious software called MacDefender that targets Mac users. While this is a new phenomenon, it has nothing to do with the security of Mac OS X. Macs are still not susceptible to viruses.
Ever since Mac OS X was introduced over ten years ago, Mac owners have watched from afar as Windows users have suffered through viruses and spyware. There are always bugs and holes in any kind of software, but Mac OS X has remained free of self-installing viruses for a decade. In light of the recent MacDefender outbreak, many people are declaring the end of Apple’s virus-free reign. The problem with these claims is that Mac OS X’s security has not actually been breached. In fact, users themselves are giving explicit permission for this software to install.
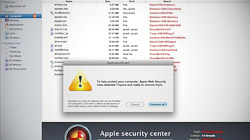
For those who are unaware of the MacDefender issue, many people with Macs have been coming across malicious webpages that trigger a download of unwanted, fake antivirus software. Many times, these webpages fraudulently claim that a security scan has found malware on the user’s Mac. The solution, they say, is to install their software, pay for it with a credit card, and run it to clean out the system. Obviously, this is all a big scam to get money and credit card numbers. The MacDefender program does absolutely nothing but pester people for payment and open adult sites if they don’t comply. While this sounds bad, there’s not much Mac OS X could have done to prevent it from happening.
Unlike Windows malware and viruses that install themselves with no interaction from the user, this new Mac trojan requires the user to do most of the work. Here’s what must happen for MacDefender to be installed on a Mac:
- The user must go to an infected website. Many people have come across these through Google Image searches, so it could happen to anyone.
- The infected page runs a script that downloads the MacDefender installer file. Most of the time, this is the end of the line. Nothing has been installed and the Mac has not been infected. Just drag the file to the Trash – no harm, no foul. However, if Safari is set to “Open ‘safe’ files after downloading,” the process moves to stage 3.
- When Safari is configured to automatically open downloaded files, the MacDefender file will launch the application installer. Even still at this point, nothing harmful has occurred. If the user wisely realizes this is not a trusted or desired installation, they can quit the installer. Again, the file can then be trashed and the whole thing can be forgotten. On the other hand, if the user chooses to click the buttons to select a destination disk and continue the installation, they move to stage 4.
- Mac OS X, as a built-in layer of security, will then ask for an Administrator password. The user must willingly enter this password to complete the installation, otherwise it will fail and MacDefender won’t infect the system. Some new variants of the MacDefender malware don’t require a password if an Administrator account is being used, though. But Apple has always recommended people create Standard user accounts for day-to-day use, which would still require a password. Regardless of the type of account, the user must still manually click through the installer to get to this point.
- Assuming the user has completed all of the previous stages and is using an Administrator account and/or has entered their password, the MacDefender trojan will finally be installed. At this point, adult sites and security scare tactics will try to persuade the user to provide their credit card information.
As you can see, the process a user must go through to infect their Mac with MacDefender requires a number of poor decisions. Specifically, decisions where the user explicitly circumvents Mac OS X’s built-in security measures and their own best judgement. This method is called social engineering – manipulating a person (by scaring them into thinking they are infected with a virus) into doing something they don’t want to do (installing malicious software that poses as something else). Social engineered malware differs from the majority of traditional Windows malware, which can install itself without the user doing a thing. MacDefender doesn’t take advantage of a weakness in Mac OS X, but rather a weakness in the user. That’s why Macs continue to be virus-free and third-party security software still isn’t needed for most folks.
Of course, that isn’t to say Apple can’t make some improvements. For one, the “Open ‘safe’ files after downloading” setting in Safari should not exist. It’s highly recommended that every Safari user go to the program’s Preferences menu and uncheck this option right now. Second, Apple should modify Mac OS X setup process to create a Standard user account by default. This is more secure because a password is required for all software installations under a Standard account. Administrator accounts should remain hidden so unknowing users don’t log into them for everyday use. Nonetheless, these are relatively minor gripes. The major issue here is training users so they are better prepared not to fall for social engineering scams.
To sum everything up, this is a human attack, not a computer attack. How can a Mac – or any piece of technology, for that matter – protect users from themselves? Aside from turning Mac OS X into a curated platform like iOS where every piece of software must be approved by Apple through the App Store, there is no way to do this. Users must stay aware of what’s going on and use their best judgement. If you don’t have antivirus software installed and you get a warning that a scan has revealed security issues, don’t believe them. If an installation starts and you don’t know what program it is or why it’s there, quit it. Most importantly, if something is asking for your Mac’s Administrator password and you don’t know why, don’t give it.









October 10th, 2011, 9:00 AM
Wow, talk about a deceptive post. To say “Macs are still not susceptible to viruses” is flat out wrong. Just because there are no widespread viruses out there does not guarantee safety.
That aside…I’d be willing to be the vast majority of malware on Windows PCs is also user-installed. Same tricks, and they’re done because people are naive when it comes to installing software. Saying “you should have known better” doesn’t eliminate the fact that there IS mac malware out there. Telling people that they’re “safe” only makes the problem worse, because then they’re MORE likely to believe the software trying to install itself.
No one I know runs as a standard user. My Mac did not suggest it when I did the initial setup. To say “Apple has always recommended people create Standard user accounts for day-to-day use” proves nothing regarding security. (Microsoft also recommends the same thing, but no one listens to them either)
In short, you do mac users a disservice with this kind of propaganda. Tell them that while there are no self-spreading viruses out there, they still need to be wary of malware that does target macs.